Iceberg Races
Posted on 2010-04-12 22:03 in Blog • Tagged with competition, programming
On Friday night (April 9th), I held my second programming competition at NDSU. This year’s turnout was much better than last year.
The Game
Iceberg Races is you’re run of the mill racing game. Players control a car which they try to navigate through the race to complete laps. When the game starts, the players are sent a copy of the map, and during each turn, they are provided location and velocity details for all the vehicles on the track. The competitor’s goal was to write an AI to find the best path through the map to win the race.
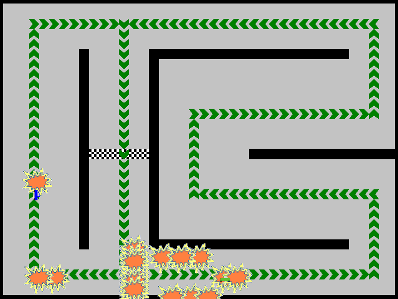
Participants
This year 22 people participated, including students from NDSU, MSUM, and Concordia. I believe all of the participants were undergraduates. All competitors came in blind. The only details that were released about the game ahead of time were clients were being provided in both Java and Python.
Problems
I was in contact with the NDSU ACM which arranged all the logistics of the actual event. They reserved rooms, provided advertising, and setup the competition computers. I had told them I needed Python and Pygame installed on the server machine. Upon launching the game, it was immediately discovered that I needed Python 2.6 and the server had 2.5.7. We spent the better part of half an hour trying to get 2.6 to install (it was not in the repositories for the distro). We eventually gave up and my laptop became the game server.
There were problems distributing the client source files. I had packaged Python and Mercurial binary libraries for use with Windows machine development (which I neglected to remove after learning the competition was being held in a Linux computer lab), this pushed the size of the source zip file from 500 Kb to 54MB. SimpleHTTPServer (Python library server) immediately crashed handling the sudden load from the downloads.
Competition
After five hours of development, all coding work came to a stop and the competition bracket was drawn up and the fierce battles began. Several clients performed excellently, some drove randomly, and a few simple spun in place. Overall, everyone had a great time watching the matches.
Winners
| Place or Achievement | Winner’s Name | Prize | Notes |
|---|---|---|---|
| 1st | Nick Laney | $75 Best buy card | |
| 2nd | Kevin Schroeder | $50 Best buy card | |
| 3rd | Ben Bechtold | $25 Best buy card | |
| Most Code | Tom Gardiner | Box of 20 Candy Bars | >400 Lines |
| Least Code | Sam Sussman | RC Car | 8 lines |
| Crash test dummy (most wall impacts) |
Andrew Dahl | Text Book | 408 |
| Speed demon (most time at full speed) |
Ben Bechtold | Text Book | 638 |
Source Code
Full source code for the server and clients, as well as all game artwork can be found in the mercurial repository hosted on Assembla.
hg pull http://hg.assembla.com/icedberg_races
I’ve also included the source for the first and second place clients (both part of the Java client).
Usage:
Clients:
java Main <name> <server IP> <server port> [ai, first, second]
python Main.py <name> <server IP> <server port>
Server:
python Main.py <port>
Acknowledgements
| Person | Reason |
|---|---|
| Nick Laney (NDSU ACM Chair) | Event running advertising and reserving the room. |
| Bethany Schlenvogt | Vehicle graphics |
| All participants | For showing up, the competition would not have been successfully without you. |
Continue reading